Maximizing Company Security: The Ultimate Guide to Electronic Safety And Security Solutions
In the fast-paced and ever-evolving landscape of business protection, the reliance on electronic safety and security services has actually ended up being vital for safeguarding beneficial possessions, confidential information, and preserving operational continuity. In this guide to digital protection remedies, we will certainly discover the most current patterns, sophisticated innovations, and finest techniques to fortify your business against possible dangers and vulnerabilities.
Significance of Electronic Protection Solutions
When thinking about the defense of possessions and delicate details, the relevance of electronic protection services can not be overstated. In today's interconnected world, where cyber hazards are regularly progressing and ending up being much more sophisticated, organizations should focus on carrying out robust digital safety and security actions to guard their information and procedures. Electronic safety services include a wide variety of modern technologies and techniques developed to protect versus unauthorized access, data breaches, malware, and other cyber risks.
One of the crucial benefits of electronic protection solutions is their capacity to give real-time surveillance and hazard discovery. BQT Sideload locks. Through tools like intrusion detection systems, firewalls, and protection info and event management (SIEM) systems, companies can proactively recognize and reply to security incidents prior to they intensify right into major violations. Additionally, electronic protection remedies aid make certain conformity with market policies and standards, safeguarding organizations from potential legal and economic consequences
Sorts Of Electronic Security Solutions
Provided the crucial value of digital security services in protecting companies against cyber dangers, it is vital to explore the different kinds of electronic safety systems readily available to enhance protection and durability. One of the most typical kinds of electronic security systems is the firewall, which acts as a barrier between a company's interior network and external networks, filtering out potentially harmful data. By using a combination of these electronic safety systems, organizations can develop a robust defense against numerous safety and security hazards.
Implementing Gain Access To Control Steps
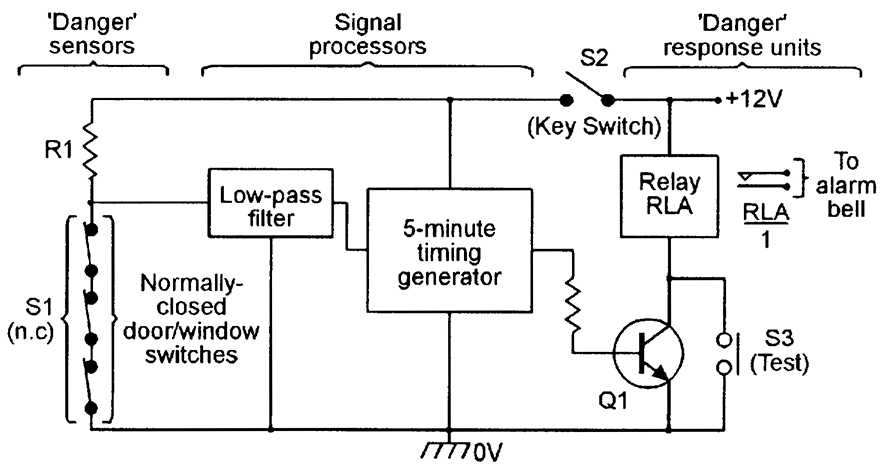
Furthermore, gain access to control steps can be incorporated with monitoring systems to check and tape people' activities within safeguarded areas. This integration enhances safety by giving a detailed introduction of that is accessing certain areas important source at any kind of offered time. Access control systems can be configured to restrict access based on time, area, or private qualifications, enabling services to tailor protection protocols according to their specific demands.
Cybersecurity Best Practices
To boost general security posture, executing robust cybersecurity ideal methods is imperative in guarding digital properties and data honesty. One fundamental technique is making sure routine software program updates throughout all devices and systems to spot vulnerabilities without delay. Using solid, one-of-a-kind passwords and applying multi-factor authentication adds layers of protection against unapproved accessibility. Conducting regular security audits and analyses helps recognize weaknesses and areas for enhancement. Employee training on cybersecurity recognition is critical in stopping social engineering assaults and guaranteeing a security-conscious labor force.
Establishing a comprehensive incident response strategy enables swift and efficient reactions to safety breaches, lessening possible damage. Securing sensitive data both in transit and at rest provides an additional barrier versus information breaches. Implementing gain access to controls based upon the principle of the very least privilege restricts the exposure of crucial systems and details to only those that require it you can find out more for their roles. Regular back-ups of data ensure that in the event of a ransomware strike or data loss, essential information can be recovered. Accepting a positive approach to cybersecurity with continual tracking and threat knowledge aids spot and minimize possible dangers prior to they escalate. By incorporating these ideal techniques right into cybersecurity techniques, companies can fortify their defenses against developing cyber hazards.
Surveillance and Monitoring Solutions

Video monitoring solutions use remote surveillance abilities, permitting authorized workers to watch on the facilities even when off-site. In addition, advanced attributes like movement detection, face acknowledgment, and license plate recognition enhance the total security posture of the company. Incorporating surveillance systems with alarm systems and gain access to control better enhances the safety and security facilities, making it possible for a positive response to potential safety breaches.
Final Thought
In final thought, digital safety services are necessary for maximizing service protection. It is vital to invest in the right electronic security systems to make sure the safety and security of the company.